WannaCry, a recent ransomware attack, is impacting organizations worldwide, with losses estimated at $4B in more than 150 countries. The combination of a ransomware executable along with worm like propagation using vulnerability exploitation makes it a very deadly cyberattack. Modern zero-day and evasive malware require a new approach to detect.
SecondWrite has built a cutting-edge sandbox that is setting a new standard in detecting zero-day and evasive malware. It captures WannaCry’s core behavior and deems it ransomware, without any signatures or training. Several of our customers have been successfully using our cloud sandbox to understand WannaCry and its variants. It captures several indicators for WannaCry using SecondWrite’s unique binary analysis and rewriting technology. It gave it a maliciousness score of 10/10, with 100% confidence that it is malware.
Below we show three images, showing what the SecondWrite sandbox tool automatically outputs for the WannaCry malware:
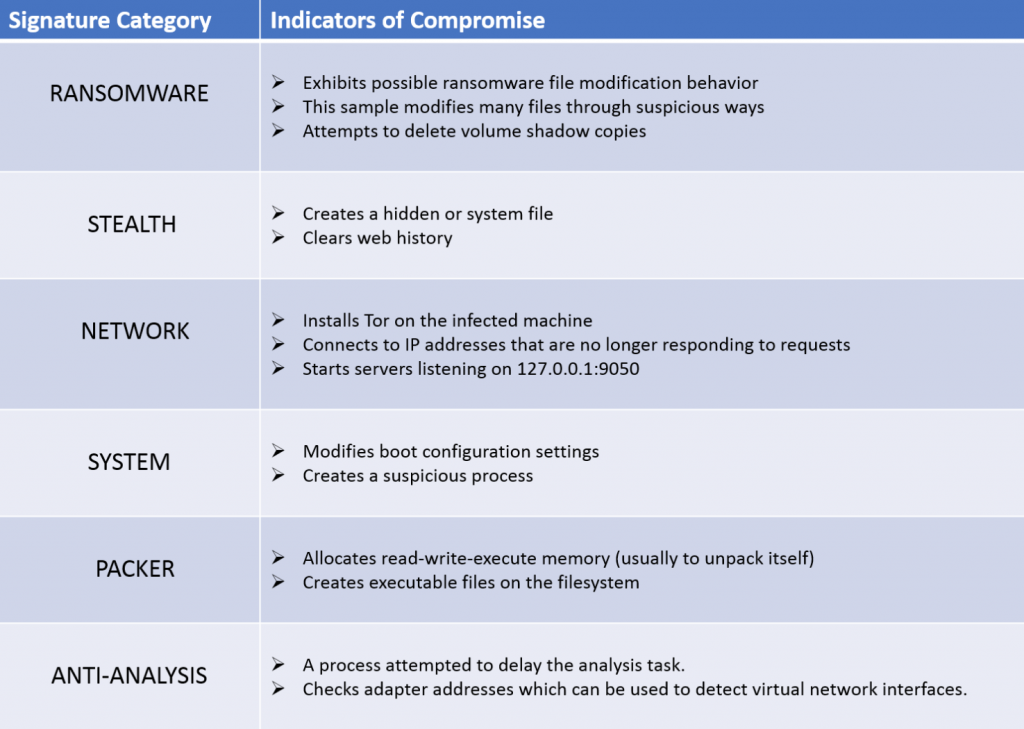
- Detects more than 30 indicators of compromise (IOCs) that are . A subset is shown in the table below.
2. Here is the Network Map the tool constructs, showing the connections, C&C requests and DNS queries made by this malware.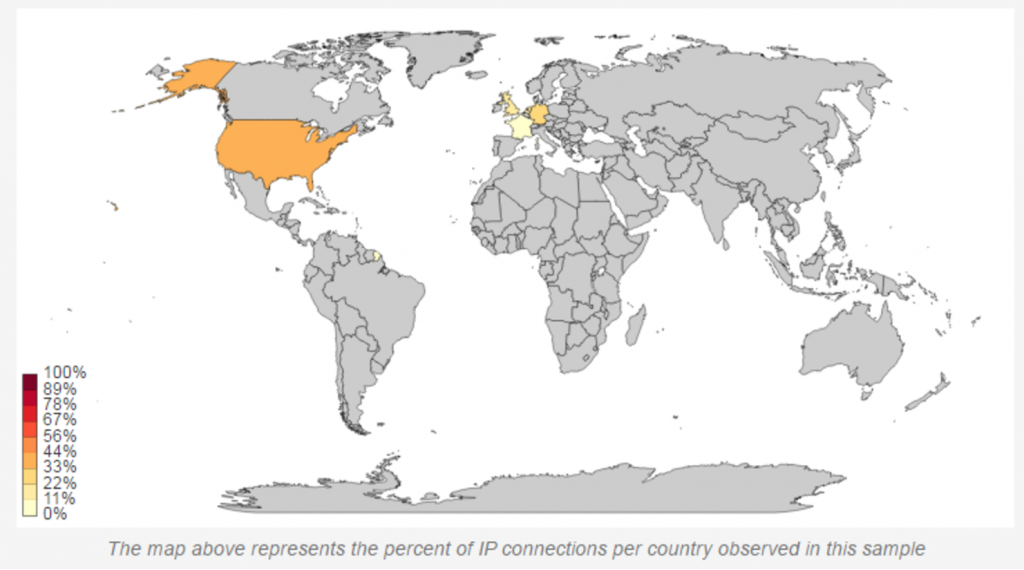
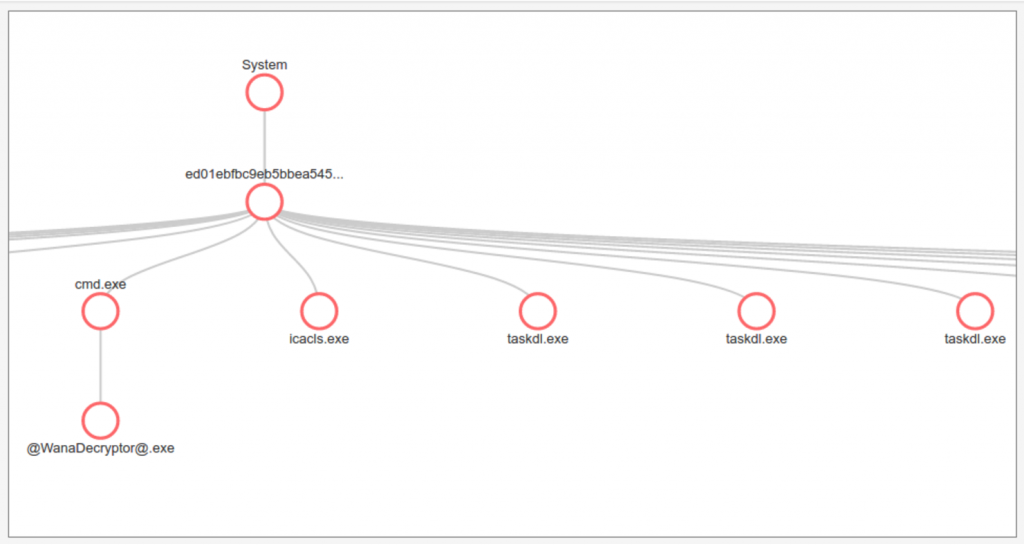
3. Here is a portion of the complete process behavior graph showing the creation of the Malware’s helper processes that do the encryption: