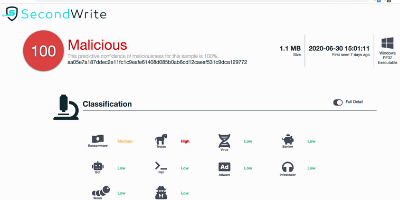
aa05e7a187ddec2e11fc1c9eafe61408d085b0ab6cd12caeaf531c9dca129772 (SHA-256)
Malicious with 100% Confidence
As WastedLocker, the newest ransomware, remains in the news; SecondWrite believed reporting on the details of its behaviors would be valuable. Symantec identified a wave of associated attacks against US companies where the end goal was to demand millions of dollars in ransom after encrypting the victim’s computer.
SecondWrite’s DeepView Sandbox analyzed this file last week and, of course saw as Symantec reported, reported it to be malicious based on its dynamic behaviors. A link to the full report from our Sandbox with detailed descriptions of those behaviors is below.
Some key highlights and indicators follow.
Type of Malware: Ransomware
- Attempts to delete volume shadow copies
- A process created a hidden window
- Allocates read-write-execute memory (usually to unpack itself)
Evasiveness Indicators:
- Attempts to repeatedly call a single API many times in order to delay analysis time
- Queries for the computer name
- Deletes its original binary for disk
- A process created a hidden window
Other Compelling Indicators:
- Creates an Alternate Data Stream (ADS)
- Creates executable on the file system
- Reads data out of its own binary image
- Creates a service
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Defense Evasion | File Detection Hidden Window NTFS File Attributes |
Selection from The Report:
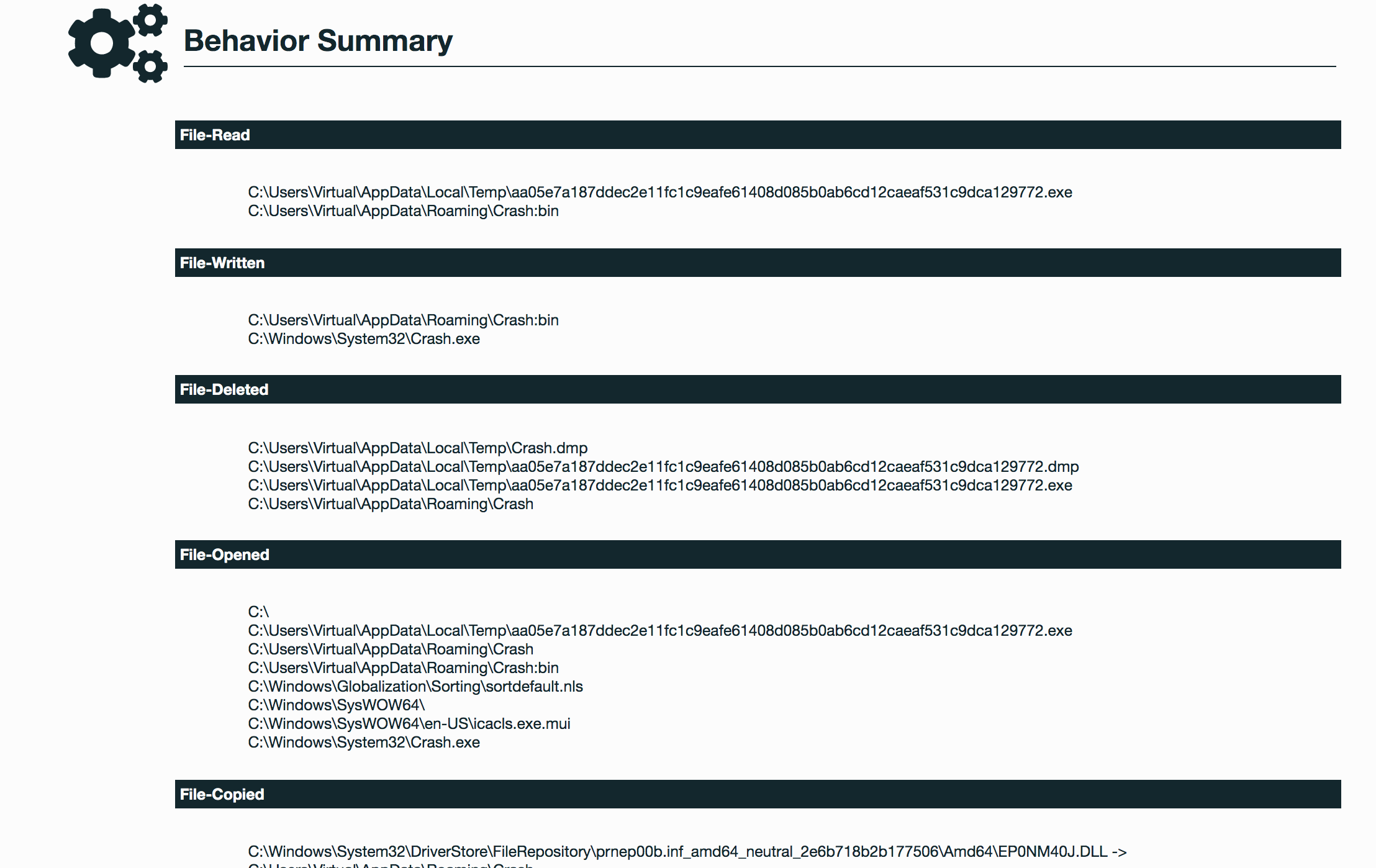
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.