1979d07792f6dbbdfda182b81adca3d5f19f87422fc70754a5989a1afb659c1b (SHA-256)
Malicious with 100% Confidence
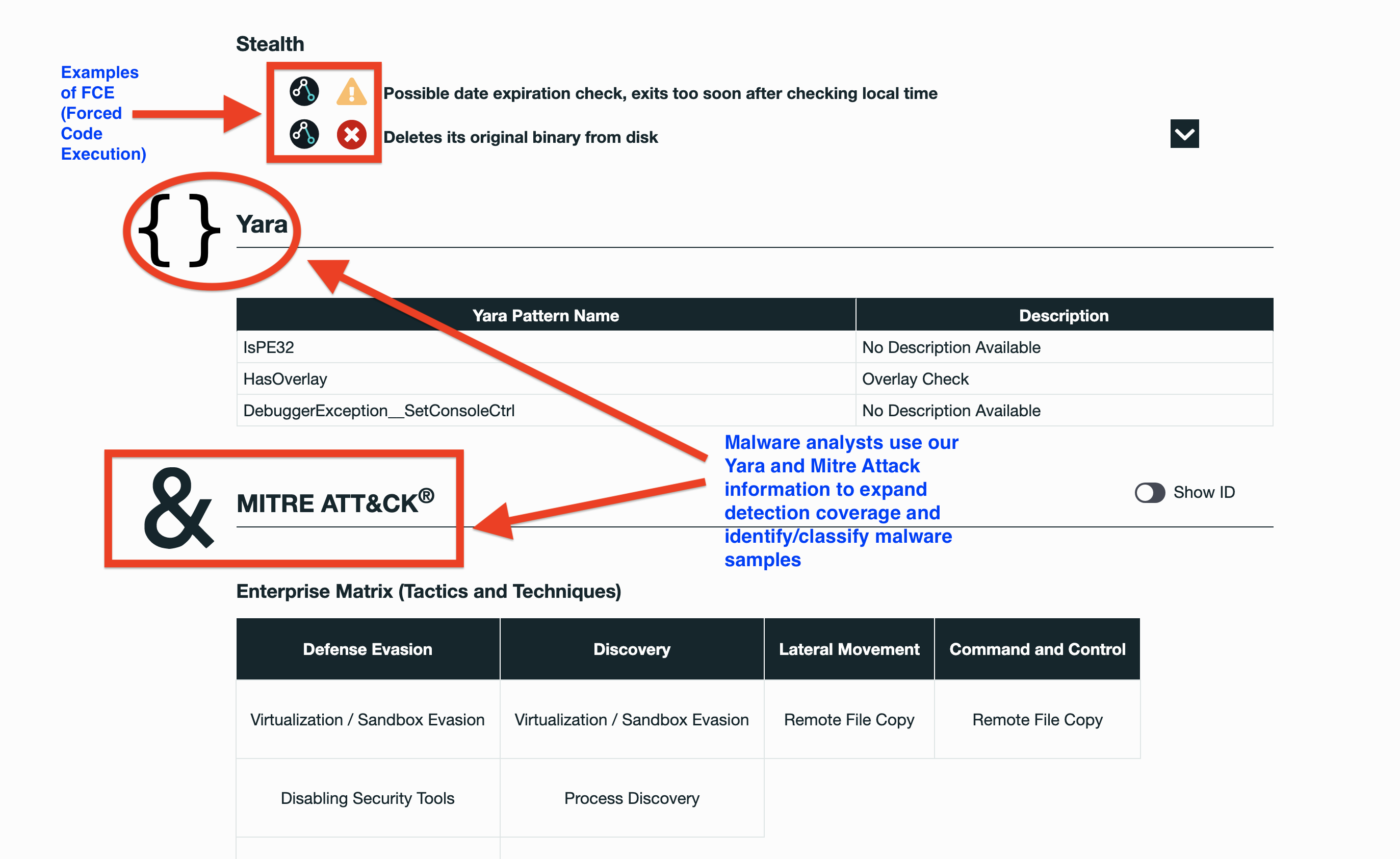
SecondWrite’s DeepView Sandbox analyzed this file – a Windows PE32 Executable – this week and declared it to be malicious. DeepView unique and patented methods identified 4 indicators – specifically force code execution (FCE) and automatic sequence detection (ASD).
A link to the full report with descriptions and details is below. Some key highlights and indicators follow.
Type of Malware: BOT
- Drops a binary and executes it
- [FCE] Deletes its original binary from disk
- Creates a slightly modified copy of itself
- Creates executable files on the filesystem
- Presents an Authenticode digital signature
Evasiveness Indicators:
- [FCE] Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available process attempted to delay the analysis task
- [FCE] Possible date expiration check, exits too soon after checking local time
- A process attempted to delay the analysis task
Other Compelling Indicators:
- [ASD] Automatic Sequence Detection maliciousness score: 68%
- Performs some DNS requests
- Anomalous binary characteristics
- Repeatedly searches for a not-found process, you may want to run a web browser during analysis
- Reads data out of its own binary image
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Command and Control | Remote File Copy |
| Lateral Movement | Remote File Copy |
| Discovery | Process DiscoveryVirtualization / Sandbox Evasion |
| Defense Evasion | Software PackingFile DeletionDisabling Security ToolsVirtualization / Sandbox Evasion |
Selection from The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.
