d590e543b70f2a94028931c414108c2282af7de162659d3978460b0adf3765a7 (SHA-256)
Malicious with 98% Confidence
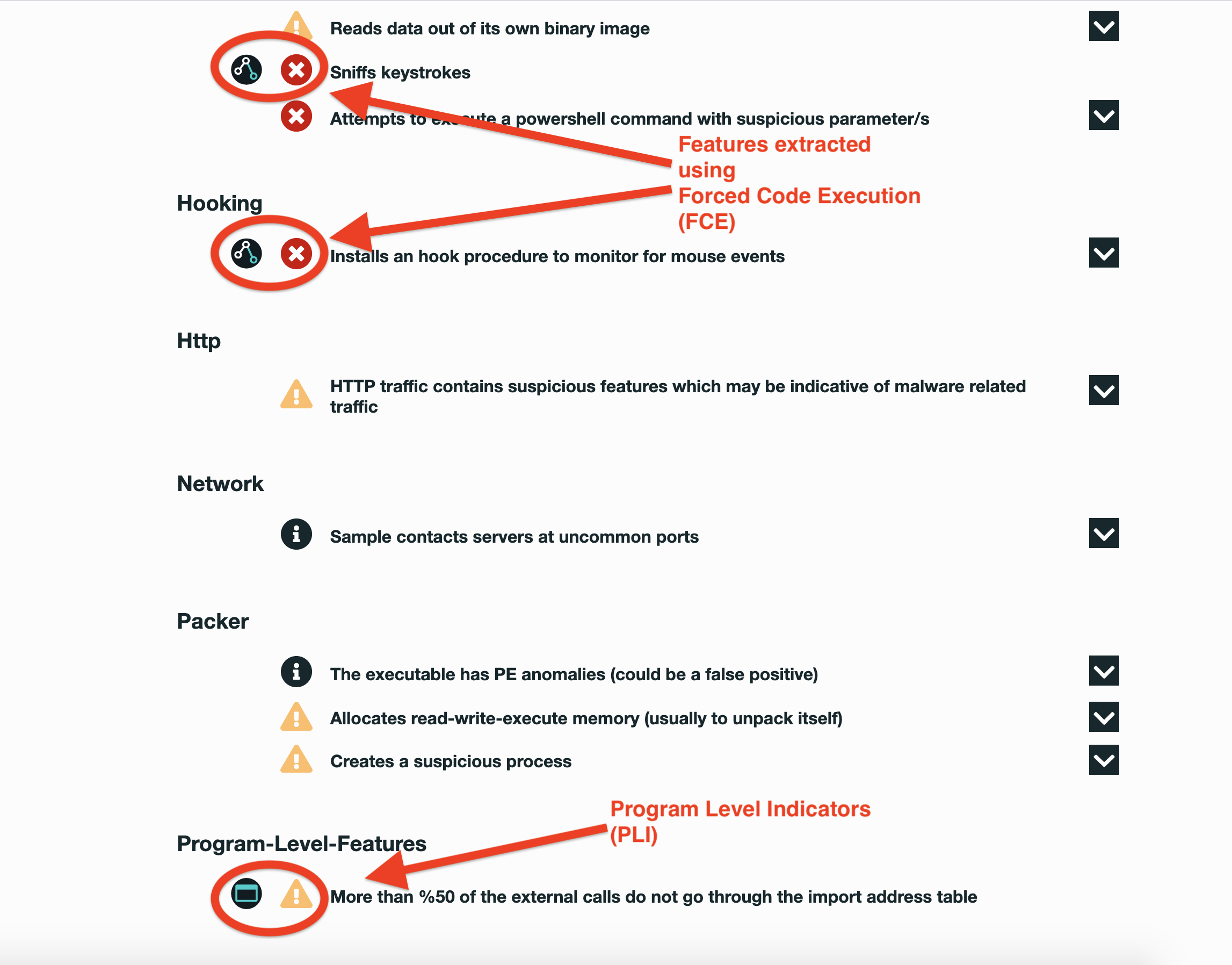
SecondWrite’s DeepView Sandbox analyzed this file this week and declared it to be malicious. At the time of its discovery, all major malware detection vendors had not identified this file of malicious. DeepView unique and patented methods – specifically in this case, force code execution (FCE) and program level indication (PLI) – identified 4 indicators. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow. Those discovered by DeepView proprietary method are flagged with [FCE] for forced code execution and [PLI] for program level indication.
Type of Malware: Trojan
- [PLI] More than %50 of the external calls do not go through the import address table
- Creates a suspicious Powershell process
- Creates executable files on the filesystem
- One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.
- Attempts to execute a powershell command with suspicious parameter/s
Evasiveness Indicators:
- [FCE] Installs an hook procedure to monitor for mouse events
- [FCE] A process attempted to delay the analysis task.
- Attempts to repeatedly call a single API many times in order to delay analysis time
- Checks adapter addresses which can be used to detect virtual network interfaces
- Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available
- A process created a hidden window
Other Compelling Indicators:
- [FCE] Sniffs keystrokes
- HTTP traffic contains suspicious features which may be indicative of malware related traffic
- Creates a hidden or system file
- Queries for the computername
- Reads data out of its own binary image
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Execution | Scripting |
| Persistence | Hidden Files and Directories |
| Defense Evasion | Software PackingVirtualization / Sandbox EvasionHidden WindowScriptingHidden Files and Directories |
| Credential Access | Credential Dumping |
| Discovery | Virtualization / Sandbox Evasion |
| Command and Control | Uncommonly Used PortCommonly Used PortCustom Command and Control Protocol |
Selection from The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.
