4b08f1847d1356be5a729869a2a73d67fcc98350513d05a505c430d888ad1f9f (SHA-256)
Malicious with 98% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious using our proprietary techniques. At the time of detection, this malware did not appear on many of the leading malware blacklists. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow:
Type of Malware: Adware
- Attempts to modify Internet Explorer’s start page
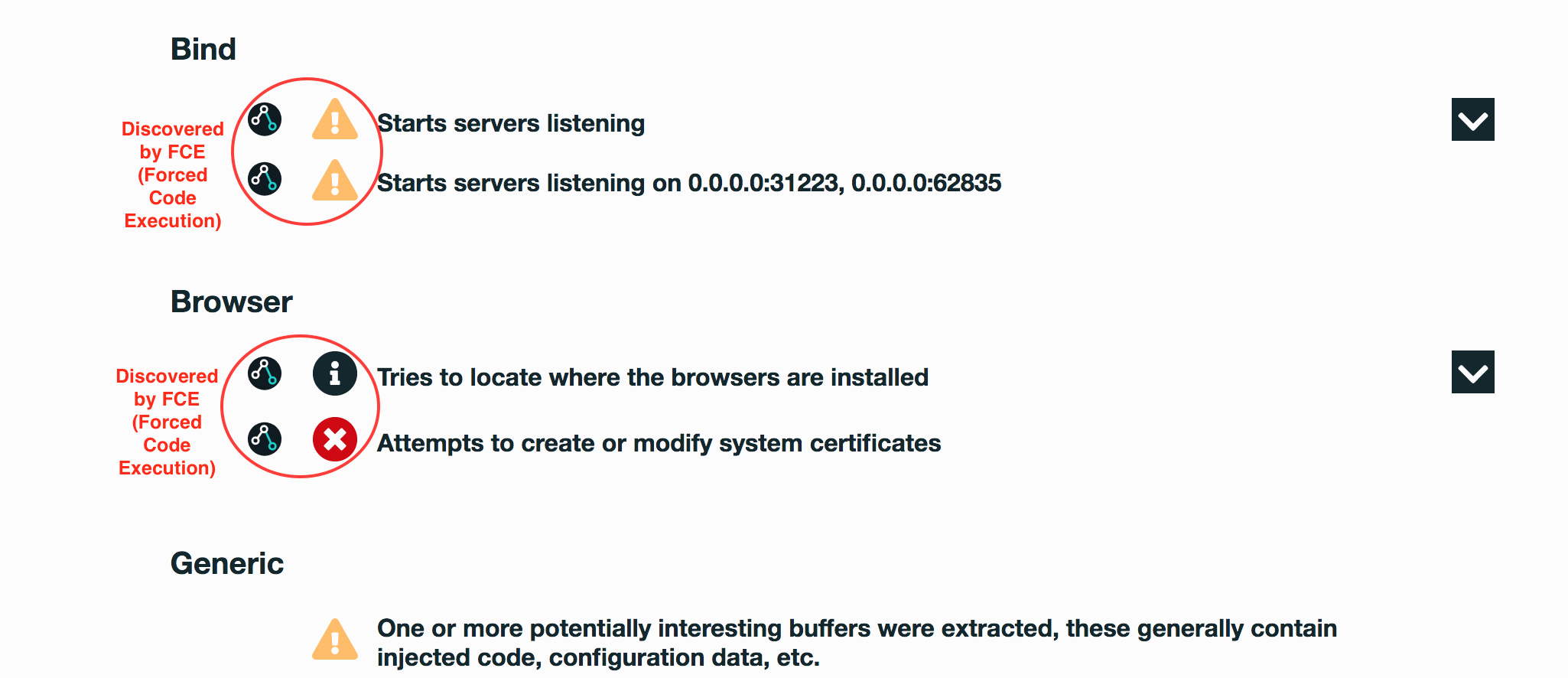
- Starts servers listening
- Tries to locate where the browsers are installed
- Attempts to create or modify system certificates
- Creates a service
Evasiveness Indicators:
- Likely virus infection of existing system binary
- Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation
- Attempts to repeatedly call a single API many times in order to delay analysis time
- Checks whether any human activity is being performed by constantly checking whether the foreground window changed
- Queries for the computer name
Other Compelling Indicators:
- Unconventional language used in binary resources
- More than %50 of the external calls do not go through the import address table
- A process attempted to delay the analysis task
- Reads data out of its own binary image
- Sample contacts servers at uncommon ports
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Discovery | Virtualization / Sandbox Evasion Process Discovery Security Software Discovery |
| Defense Evasion | Software Packing |
| Command and Control | Remote File Copy Uncommonly Used Portl |
Selection from The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution,Program Level Indicators, and Automatic Sequence Detection
