17e826fa0f6297f80b459948ab12efbdefc06f3cb999184a5cb1eddcf7b7d550 (SHA-256)
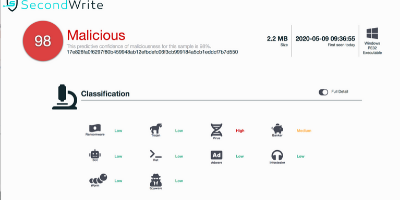
Malicious with 98% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious using our proprietary techniques – which in this case revealed 5 indicators of significance. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow:
Type of Malware: Banker
- Creates known Dyreza Banking Trojan files, registry keys and/or mutexes
- Sample contacts servers at uncommon ports
- Tries to locate where the browsers are installed
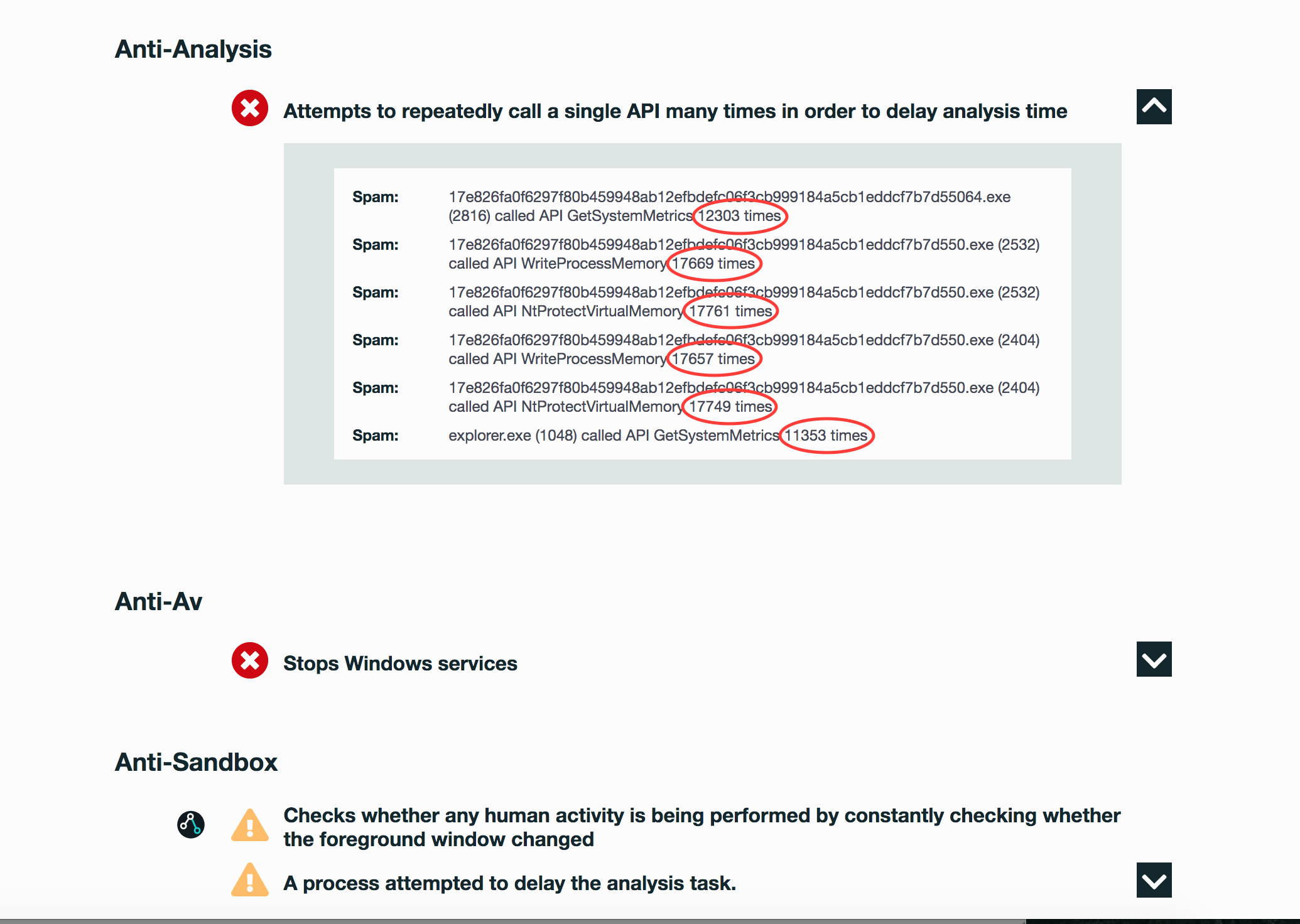
Evasiveness Indicators:
- Sniffs keystrokes
- Detects VMWare through the in-instruction feature
- Checks whether any human activity is being performed by constantly checking whether the foreground window changed
- A process attempted to delay the analysis task
- Checks adapter addresses which can be used to detect virtual network interfaces
Other Compelling Indicators:
- Drops a binary and execute
- One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.
- Contains obfuscated control-flow to defeat static analysis
- Deletes its original binary from disk\
- Strings possibly contain hardcoded IP Addresses
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Command and Control | Remote File Copy Custom Command and Control Protocol Remote File Copy Uncommonly Used Port |
| Credential Access | Credential Dumping |
| Defense Evasion | Code Signing File Deletion NTFS File Attributes |
| Discovery | Process Discovery6 Virtualization / Sandbox Evasion |
| Impact | Service Stop |
Selection from The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.