d79e4c4ceb3abc8a51a01eff14a51694d7c25f9306ee71a922a01fddb48a15fe (SHA-256)
Malicious with 100% Confidence
SecondWrite’s DeepView Sandbox analyzed this file – a Windows PE32 Executable – this week and declared it to be malicious. At the time of its discovery, all major malware detection vendors had not identified this file as malicious. DeepView unique and patented methods identified 2 indicators – specifically in this case, automated sequence detection (ASD) and program level indication (PLI).
A link to the full report with descriptions and details is below. Some key highlights and indicators follow.
Type of Malware: Ransomware
- [ASD] Automatic Sequence Detection maliciousness score: 56%
- Installs itself for autorun at Windows startup
- Attempts to disable UAC
- Expresses interest in specific running processes
Evasiveness Indicators:
- Deletes its original binary from disk
- Attempts to modify Explorer settings to prevent hidden files from being displayed
- Attempts to modify Explorer settings to prevent file extensions from being displayed
- A process created a hidden window
- Disables Windows Security features
Other Compelling Indicators:
- [PLI] Contains obfuscated control-flow to defeat static analysis.
- Expresses interest in specific running processes
- One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc
- Creates executable files on the filesystem
- Sample writes a large amount of files (Over 100)
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Command and Control | Uncommonly Used Port Remote File Copy Commonly Used Port Custom Command and Control Protocol |
| Defense Evasion | Virtualization / Sandbox EvasionHidden WindowNTFS File AttributesScriptingFile DeletionHidden Files and DirectoriesProcess Injection |
| Discovery | Virtualization / Sandbox EvasionProcess Discovery |
| Lateral Movement | Remote File Copy |
| Persistence | Hidden Files and Directories Registry Run Keys / Startup Folder |
| Privilege Escalation | Bypass User Account Control |
Selection from The Report:
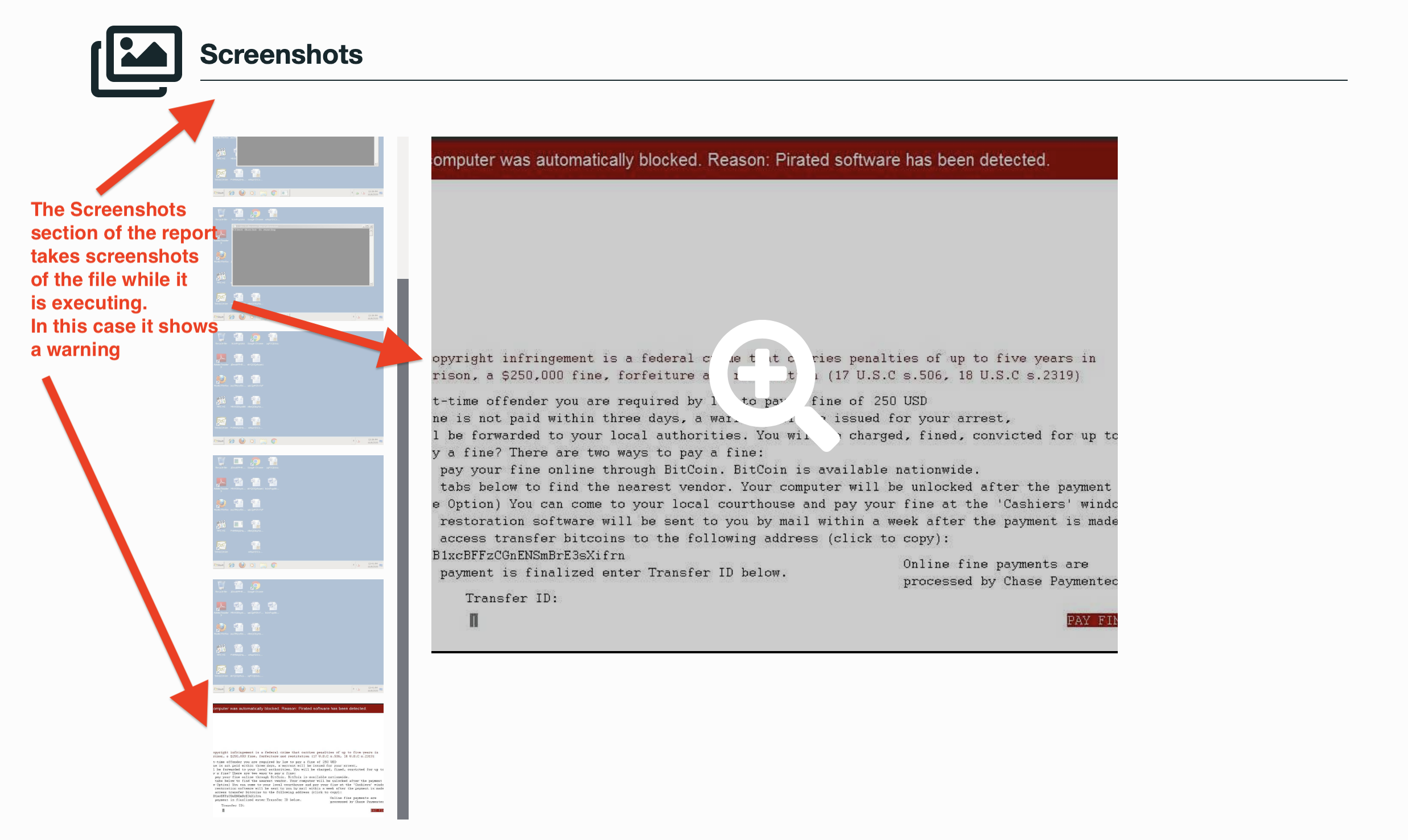
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution,Program Level Indicators, and Automatic Sequence Detection.
