289477f12b10e6b770b40d4c0fb028b1af46b295a91030793c7188abe9774d0b (SHA-256)
Malicious with100% Confidence
DeepView Sandbox analyzed this file last week and declared it to be malicious. The Sandbox’s unique and patented methods – specifically in this case, automatic sequence detection (flagged by [ASD] below) – identified 1 indicator. (ASD is one of SecondWrite’s patented methods; it uses machine-learning based on 100,000s of samples to recognize malicious sequences in code. The full DeepView Sandbox report with details can be viewed at:
REPORT HIGHLIGHTS
Type of Malware: Worm
- [ASD] Automatic Sequence Detection maliciousness scores: 76%
Evasiveness Indicators:
- A process attempted to delay the analysis task
- Checks adapter addresses which can be used to detect virtual network interfaces
Other Compelling Indicators:
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Command and Control | Common Used Port Custom Command and Control Protocol |
| Defense Evasion | NTFS File Attributes Software Packing |
| Discovery | Virtualization / Sandbox Evasion |
| Persistence | Registry Run Keys / Startup Folder |
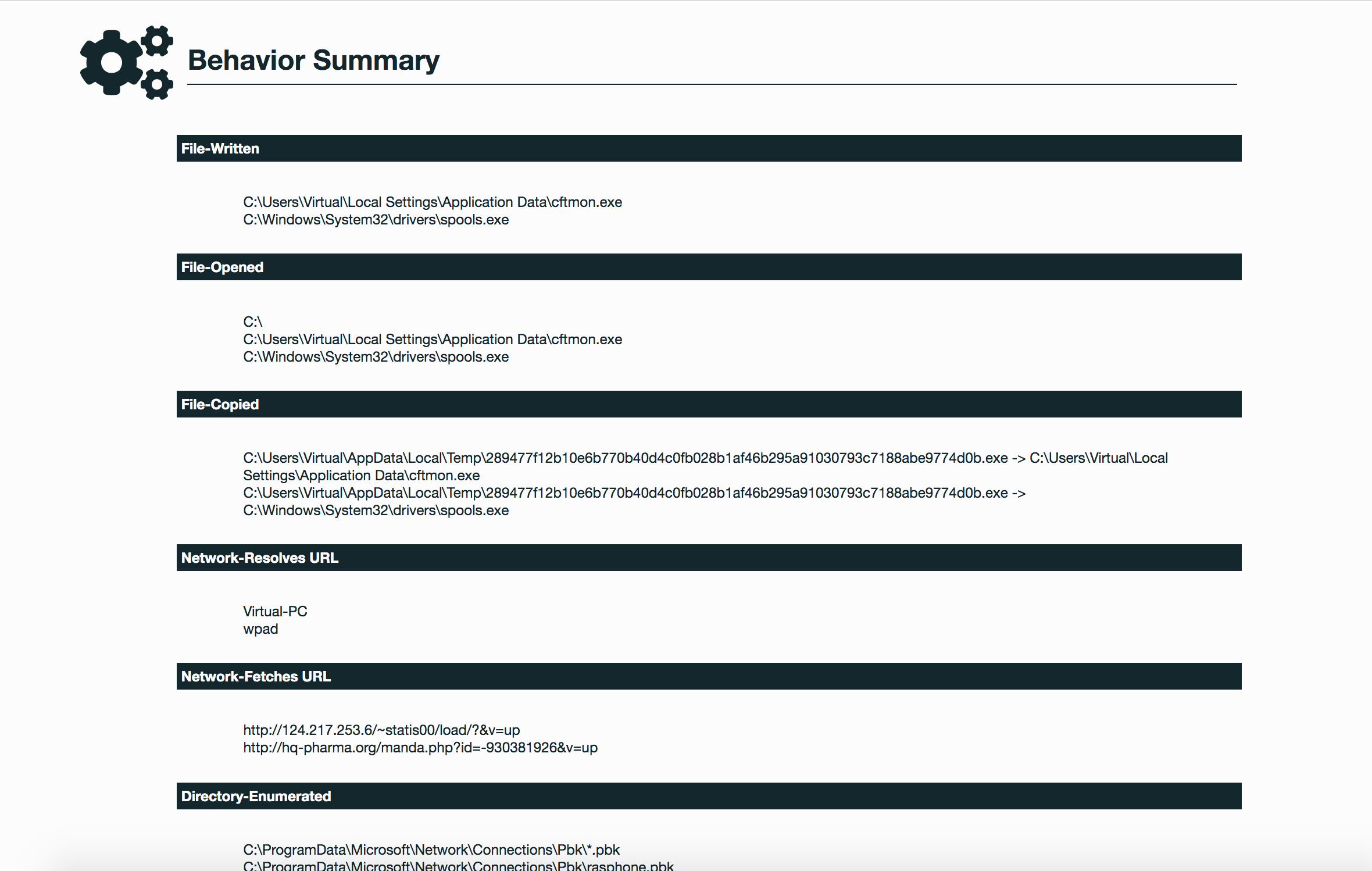
Selection from The Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution,Program Level Indicators, and Automatic Sequence Detection
